FTP
Version
vsFTPd 3.0.3
Possible Vulnerabilities


Anonymous Access

PUB directory, meaning we are most likely in this directory.
/var/ftp/pub/
We also have a pcap file.

The capture contains traffic from an internal service running on port 51072 that connects to the mongodb service running on port 27017.

I also verified that the port was indeed running internally and this was the case.
I also analyzed the pcap file to see if there was any information about the internal service such as possible version numbers but nothing.
Upload permissions are off as well.
Inside the pub directory, we find a PCAP file debug.pcap.
We'll download and examine this file.
Exploitation
MongoDB Authentication Handshake Brute-Force
Opening and viewing the PCAP file in WireShark, we can see that it contains what appears to be a MongoDB authentication handshake.
According to the MongoDB documentation, starting from version 4.0, MongoDB uses Salted Challenge Response Authentication Mechanism (SCRAM) as its default authentication protocol. MongoDB also provides a helpful blog post outlining the protocol. The protocol is also detailed in RFC 5802.
If a full exchange is captured, then an offline dictionary attack can be mounted in an attempt to crack the password. Specifically, we would need to obtain the following information: username, salt, client nonce, server nonce, and the target hash value.
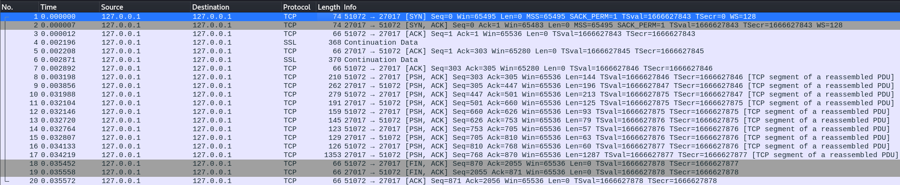
Luckily, it looks like we have the full exchange captured. The username (admin) and the client nonce (+CDTb3v9SwhwxAXb4+vZ32l0VsTvrLeK) can be found in the eighth packet.
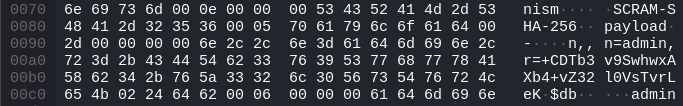
The server nonce (+CDTb3v9SwhwxAXb4+vZ32l0VsTvrLeKoGtDP4x0LH5WZgQ9xFMJEJknBHTp6N1D) and the salt (zOa0kWA/OTak0a0vNaN0Zh2drO1uekoDUh4sdg==) can be found in the ninth packet.
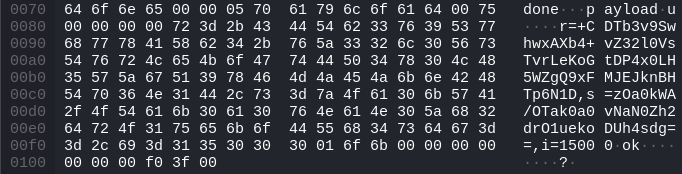
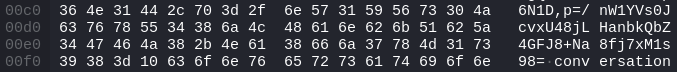
Finally, the target hash (/nW1YVs0JcvxU48jLHanbkQbZ4GFJ8+Na8fj7xM1s98=) can be found in the tenth packet.
Nice, we appear to have all the needed information to mount our dictionary attack. However, unfortunately for us, neither John nor Hashcat support brute-forcing SCRAM, so we'll have to write our own tool. In order to do that, we have to fully understand the protocol.
Because this is an offline attack, we can afford to use a larger wordlist, such as rockyou.txt. The following PoC script should crack the handshake for us within a reasonable time.
Let's give it a try.
After about 4000 iterations, our script finds the admin password to be monkey13. Let's connect to MongoDB and list available databases. To do that, we first need to install the mongodb-org-shell package by following this guide. Once the shell package is installed, we'll connect to MongoDB with the recovered credentials.
Last updated