Glusterd + Docker Container Breakout
When looking at the processes i noticed gluster running.

After some research i found gluster to be vulnerable to a local privilege escalation exploit: cve-2018–1088, this exploit will allow us to escape the docker container and fully compromise the machine.
To exploit cve-2018–1088 we basically mount a share to a share on the server containing the gcron_enabled file and add a malicious cronjob that will execute a reverse shell on the main host.
![]()
creating the share to mount to the host
![]()
mounting the share through gluster
![]() creating the scheduled task to be executed
creating the scheduled task to be executed![]()
creating the malicious payload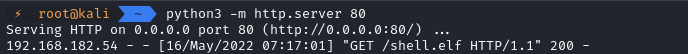
cronjob downloading my malicious executable
gaining full compromise
Last updated